When employees leave, does their access truly leave with them?
In today’s hybrid and high-turnover environments, employee exits are frequent and often unpredictable. Every dispensable access can become a potential compliance violation, data breach, or insider threat.
This blog explores the real risks of poor offboarding management. Know why automation is critical, and how Hire2Retire enforces secure and timely offboarding automation.
As the tech space becomes extremely dynamic with frequent new employee hiring, role changes, and terminations, automated SCIM provisioning is no longer a luxury; it is a necessity.
Security conversations in organizations often focus on external threats, like firewalls, endpoints, or SSO. But one of the most overlooked vulnerabilities lies within the organization itself; incomplete offboarding.
Here are 5 persisting risks of manual offboarding:
Even a 24-hour delay in access revocation creates opportunities for data misuse, especially when credentials remain active across critical systems like CRM or cloud storage. Most organizations can’t manually track these oversights until it’s too late.
Disabling user accounts is not enough. Role-based and privileged access, like admin credentials, database logins, DevOps tools, often bypass central directories and remain active. Without automation, these become persistent and costly security gaps.
Departing employees take more than just access with them; they often hold critical project context, client communications, and work-in-progress documentation.
Without a structured offboarding process to handle mailbox forwarding or OneDrive reassignment, and clear task handovers, institutional knowledge is lost. This loss of continuity leads to confusion, customer complaints, and rework, all of which can be avoided with offboarding automation.
From a compliance perspective, offboarding is just not enough; companies need to prove it. Manual offboarding lacks standardized records that confirm when access was removed, by whom, and from which systems. In the event of an audit or security incident, the lack of an audit trail can result in fines, failed certifications, or loss of customer trust. For GRC teams, it might be a huge red flag.
Effective offboarding starts with coordination across HR, IT, Security, and in some cases, Legal. Most organizations operate in isolation, using disconnected tools, HRIS platforms, IAM systems, ITSM tickets, spreadsheets, and email threads.
Traditional offboarding relies on manual steps, cross-team follow-ups, and inconsistent execution. Off-boarding automation doesn’t just reduce effort; it also eliminates blind spots, aligns systems and people, and ensures every exit is secure, compliant, and documented.
Here’s what secure, complete, and compliant off-boarding automation does:
1.Off-boarding in Real Time: The moment an employee is marked as terminated in the HR system (Workday, SAP, Bamboo HR, or others), the off-boarding workflows trigger instantly. This closes the gap between intent and action, eliminating delays caused by ticket queues or miscommunication.
2. Identity Deactivation Across IAM & SaaS: An automated system should immediately disable the employee’s identity across connected identity providers (Okta, Entra ID, Google Workspace, or others). This consists of suspension of Single-Sign-On access, GAL removal, and revoked access to group memberships. Simultaneously, it should also revoke sessions and tokens across cloud applications, ensuring the former employee is locked out completely, without requiring IT intervention.
3. Role-Based De-provisioning: Off-boarding isn’t one-size-fits-all. A truly robust off-boarding automation process should account for contextual attributes such as job role, business unit, location, and seniority. For example, an engineer exiting from a U.S. office may require access revocation from apps like JIRA, GitHub, and internal VPNs, while a finance employee sitting in a UK office may require removal of payroll apps. Dynamic, rule-based access logic ensures nothing is missed.
4. Automated Mailbox Conversion to Shared Inbox: Email continuity is important for both internal and external stakeholders. As part of off-boarding, the employee’s mailbox should be automatically converted to a shared mailbox. This prevents communication gaps, prevents data loss, and maintains visibility over ongoing conversations, especially important in customer-facing or finance roles
Every gap we’ve explored till now, from lingering access to audit blind spots, it all comes down to one thing: a fragmented process. Hire2Retire fixes that by being a bridge between the HR system, identity providers, and downstream apps.
Here’s how Hire2Retire enforces off-boarding automation with precision, at scale:
Hire2Retire considers your HRMS, such as Workday, SAP, SuccessFactors, Bamboo HR, etc., as a single source of truth and detects sensitive termination events the moment they’re updated. This real-time HR-to-IT bridge ensures offboarding begins the second the employee leaves, and not days later when IT finally gets the time to deal with tickets.
Every organization has different rules or policies for different roles. Hire2Retire supports rule-based access policies that factor in job role, departments, location, and employment type. Whether it’s revoking access from engineering tools or finance systems, Hire2Retire ensures each identity is terminated in accordance with company’s policy and not generic rules.
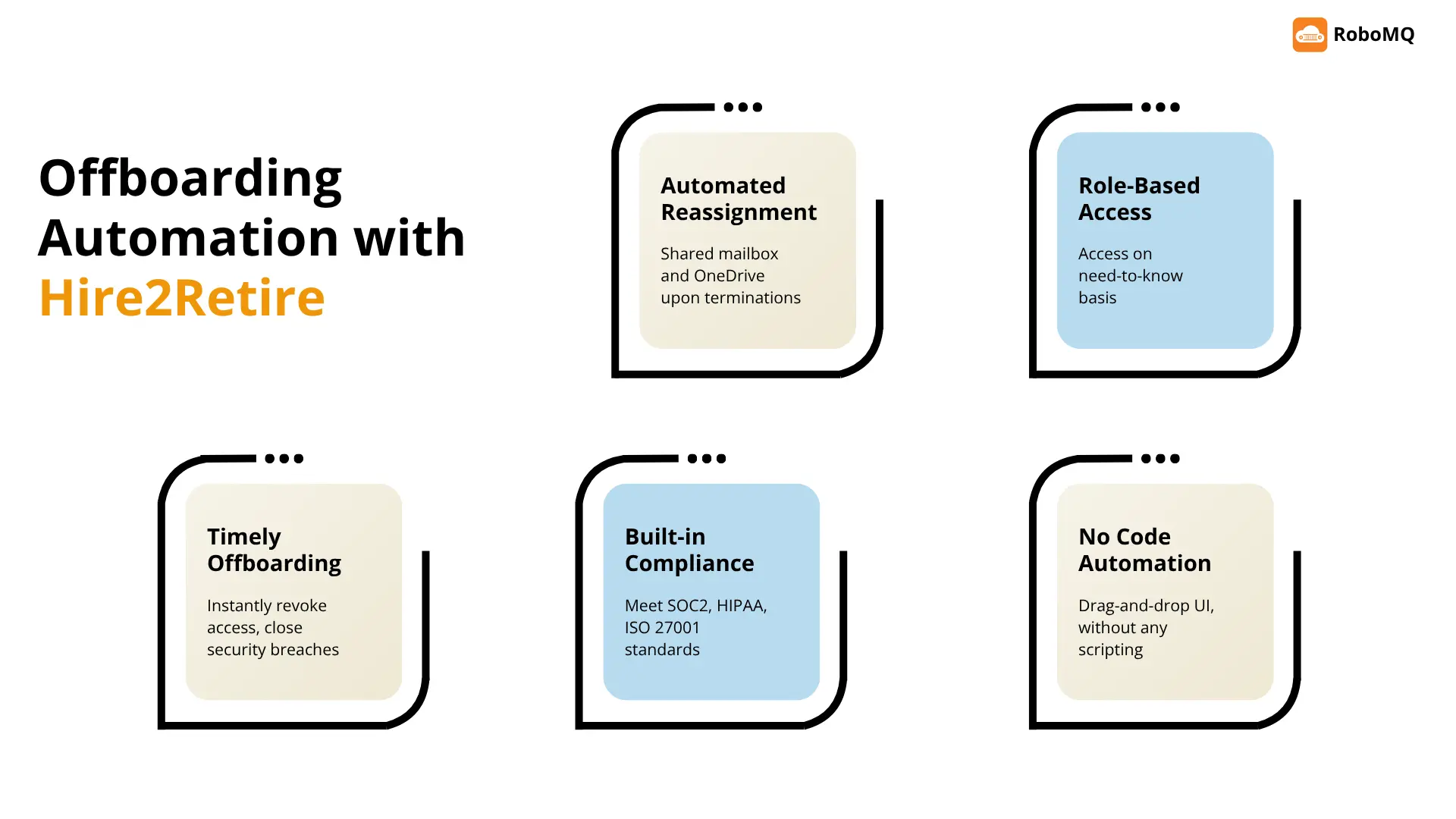
: With integrations available with IdPs like Okta, Active Directory, Google Workspace, and ITSM tools such as ServiceNow, Jira, and others, Hire2Retire automates every off-boarding task. Whether it comes to identity and group removal, license revocation, sharing mailbox, and OneDrive reassignment, everything is possible without any custom scripting. You can configure complex rules in Hire2Retire with drag-and-drop logic.
Off-boarding is a cross-functional effort. Hire2Retire can send real-time notifications to HR, IT, GRC, and other operations with Communication Hub. These alerts include task completion updates, escalation triggers, or checklist confirmations, keeping every team in the loop.
With Hire2Retire, organizations can track every event in time-stamped, tamper-proof logs. Whether it’s an internal or external security review, you’ll have a clean, traceable proof of compliance, without the effort of compiling data from five different systems.
Proper Offboarding isn’t just an HR liability; it is a security, compliance and operational mandate. When done manually, it leaves behind a trail of risk. When automated with the right intelligence and orchestration, it becomes a source of control, compliance and peace of mind.

Somya Shrimal is a Marketing Specialist at RoboMQ. She is a tech enthusiast and a prolific blogger who helps businesses stay up-to-date with the latest trends and best practices in the industry. Her expertise in SaaS, cloud, on-premises apps, and IoT has made her a go-to source for businesses looking to navigate the ever-changing tech landscape.

Somya Shrimal is a Marketing Specialist at RoboMQ. She is a tech enthusiast and a prolific blogger who helps businesses stay up-to-date with the latest trends and best practices in the industry. Her expertise in SaaS, cloud, on-premises apps, and IoT has made her a go-to source for businesses looking to navigate the ever-changing tech landscape.