It is Ben’s first day at work at a well-known medical institution as a Marketing Analyst. His manager assumed that the company’s IT team would provision his access before his joining to ensure he had access to shared drives and tools. However, Ben is unable to log into the reporting tool, and he does not have access to the shared marketing SharePoint folder either. After multiple emails and follow-ups, Ben could log into company CRM three days later.
However, on the flip side, having no role-based access control, the credentials of former Market Analyst, Monica, who was terminated 3 weeks ago, are still active. She still has access to the SharePoint site, and her HubSpot account is still not deactivated. The ghost account of Monica exposes their business to intense security risk and data breaches. This isn’t a unique case, many organizations globally are still managing employee access through spreadsheets and outdated systems. In the absence of a structured approach to access provisioning in an organization, HR and IT often struggle with avoidable issues.
In this case, automated access provisioning could have ensured that Ben had access to right tools and resources on day one. At the same time, Monica’s credentials would have been automatically disabled on her last working day itself. These are not just IT delays, these are productivity and security blockers to the organization. Organization today needs a structured and scalable way to manage access throughout whole employee lifecycle and Role Based Access Control enables exactly that.
You’ll learn how Hire2Retire automation transforms onboarding, offboarding, and role changes, streamlining service management, eliminating security risks, and letting your IT team work smarter instead of harder.
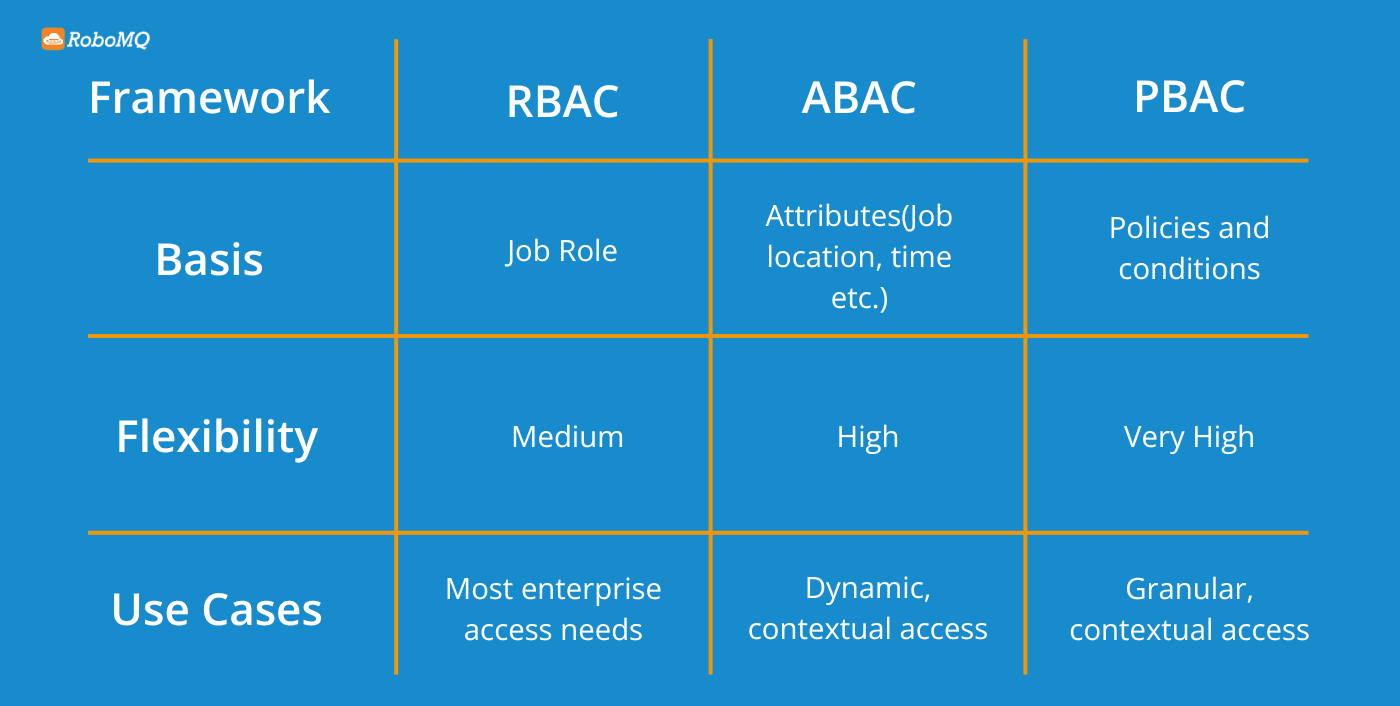
Role Based Access control (RBAC) is a powerful approach to automating access provisioning. It is a security and identity governance framework for managing identity and access. It offers structured and scalable solutions to provisioning challenges. RBAC ensures employee access is managed based on their role, not individual requests. Access and permissions are not assigned manually for the application or tool. Instead, permissions are bundled into groups associated with a role and are automatically assigned whenever a user steps into that role.
Consider the example of floor access: A “Marketing Analyst” ID will unlock the marketing floor, conference rooms, and department shared drives. However, it won’t work for patient rooms or the HOD wing. This access is assigned based on job role and not separately assigned every time.
Simplifying access management, this model minimizes provisioning errors.
In most cases, RBAC is the best starting point. The reason is as simple as it is for adoption, it is also structured for security. Frameworks like ABAC and PBAC can be adopted later for unique scenarios.
As an organization scales, managing access and permissions becomes very complicated yet critical. Manually managing employee access can work if you have 100 or 200 employees. However, for a workforce size bigger than that, it is not sustainable. RBAC helps enterprises:
Theoretically, RBAC sounds very straightforward and simple. However, implementing it for multiple disconnected systems like Active Directory, HRIS, ATS, access apps, and ITSM applications is a very complex process. That is where Hire2Retire makes everything simple and easy.
A no-code workforce lifecycle management platform, Hire2Retire enables organizations to implement Role Based Access Control seamlessly.

Here’s how it works:
Hire2Retire syncs data from your HRIS to IDP such as Active Directory, Entra ID, Okta Directory, or Google Workspace. In addition to that, it scales user provisioning across hundreds of cloud and on-prem apps.
With Hire2Retire, roles are mapped based on attributes like Job Title, Department, or Employment Type. It automatically assigns users to correct security groups, and distribution lists based on their role without manual intervention.
Hire2Retire automatically manages the entire JML cycle. As soon as an employee steps into a new role, access to necessary resources and tools is granted in real-time. When an employee changes roles and shifts departments, outdated permissions are revoked. At the same time, new permissions are granted immediately. Hire2Retire also ensures sensitive terminations. It automatically revokes access to all systems when an employee leaves an organization, ensuring compliance.
Every change done on the Hire2Retire platform can be logged and monitored. It gives you real-time visibility to your HR data making audit easy, fast, and accurate.
The story of Ben and Monica isn’t something unusual. Organizations can struggle with poor employee experience, security risks, and wasted resources in the absence of automated access governance. Suppose if the organization had RBAC in place, Ben would’ve had access to applicable tools and resources on day one without delay. Similar to 92% of new hires onboarded through Hire2Retire. On the other hand, Monica’s access would have been revoked and her account disabled on her day of termination itself. If the organization has automated access provisioning through RBAC in place, both security and efficiency dramatically improve.
For access challenges, automated Role Based Access Control is the only answer. Hire2Retire enables organizations to shift their focus from operational delays and fallbacks to strategic building and growth. Our 150+ customers around the globe swear by it.

Schedule a call with one of Hire2Retire’s experts and learn how Hire2Retire helps you implement RBAC automatically and at scale.

Somya Shrimal is a Marketing Specialist at RoboMQ. She is a tech enthusiast and a prolific blogger who helps businesses stay up-to-date with the latest trends and best practices in the industry. Her expertise in SaaS, cloud, on-premises apps, and IoT has made her a go-to source for businesses looking to navigate the ever-changing tech landscape.

Somya Shrimal is a Marketing Specialist at RoboMQ. She is a tech enthusiast and a prolific blogger who helps businesses stay up-to-date with the latest trends and best practices in the industry. Her expertise in SaaS, cloud, on-premises apps, and IoT has made her a go-to source for businesses looking to navigate the ever-changing tech landscape.