The imperative for zero trust strategy is no longer theoretical. Recent industry research shows organizations facing rapidly rising breach costs, which reached roughly $4.88M in 2024, a figure that continues to climb as attack complexity increases. At the same time, a 2024 Gartner survey found roughly 63% of organizations have at least partially implemented zero trust strategies, signalling that this is now boardroom-level risk management. Hybrid work, global talent acquisition, and operations running 24/7 have reshaped how organizations deal with workforce management. Traditional 9-to-5 employment models and outdated access methods no longer align with modern business realities.
Finally, identity remains the dominant attack vector, Verizon’s DBIR shows stolen/compromised credentials feature heavily in incidents, meaning identity controls directly affect an organization’s breach risk. Rising costs, momentum behind Zero Trust, and credential-driven attacks, explain why IT leaders must treat identity governance as foundational, not optional.
It is a simple idea with complex execution: never trust, always verify, continuously validate every user, device, and request. The NIST/CISA frameworks and maturity models make clear that zero trust is an architecture of continuous verification across people, devices, networks and workloads; identity is the pivot for those checks.
Without authoritative, auditable identity and entitlement data, policies like least privilege, adaptive access, and context-aware MFA are guesses, not controls. In other words, you can buy SSO or conditional access but if you can’t answer “who should have access to X, why, and when was it last reviewed?” you cannot operationalize it at scale.
Identity Governance & Administration (IGA) is where identity becomes a business-grade control. Core IGA capabilities, authoritative identity source (often HR), onboarding/offboarding automation, role changes, entitlement, access request/workflow, certification, and audit reporting, make zero trust policy into enforceable reality.
Gartner and market leaders consistently identify IGA as the mechanism that eliminates stale access, prevents privilege creep, and provides the attestations auditors and boards demand. Furthermore, effective IGA enables:
Least-privilege: Roles and policies mapped to job functions prevent unwarranted entitlements.
Fast deprovisioning: When an employee leaves or a contractor’s engagement ends, access is removed everywhere the moment HR signals it.
Continuous validation: Periodic checks and automated entitlement recertification ensure access decisions aren’t “set and forget.”
Adaptive access: IGA feeds identity (roles, attributes, risk flags) into conditional access engines and IAM systems.
Hire2Retire (H2R) is designed to solve the operational gaps that prevent your strategy from delivering value. For IT leaders and senior managers evaluating how to make zero trust practical and auditable, Hire2Retire provides the following high-impact capabilities:
H2R uses HR systems as a single source of truth for information on (hire, role change, transfer, termination) so identity lifecycle information is managed across different systems accurately. This alignment eliminates delays and reduces orphaned access.
H2R automates account and entitlement lifecycle, removing the window where dormant or inappropriate access can be exploited.
Hire2Retire enables RBAC/ABAC models, reducing privilege creep and enabling least-privilege by design.
It implements business-driven approval paths and scheduled certifications, so access reviews are consistent, measurable, and audit-ready.
Hire2Retire generates time-stamped logs, dashboards, and access trails of your workforce lifecycle data for internal audits and external compliance needs.
Built for scale with drag-and-drop orchestration, empowering HR and IT to manage multiple workflows without any scripting.
Zero trust security is now a board-level requirement because breaches are costlier and identity-based attacks dominate. The architecture-level guidance is clear, but success depends on operational identity governance.
IGA isn’t a “nice to have” operational capability; it’s the glue that converts policy into action. Hire2Retire is built to be that glue: connecting HR truth, automating identity lifecycle, and supplying the visibility and controls IT leaders need to make Zero Trust measurable, enforceable, and sustainable.
Ready to move from zero trust strategy to Zero Trust Security? Align your identity lifecycle to your security controls and let Hire2Retire be the engine that gets you there. Book a session with our experts to find out more.
As organizations move to hybrid and cloud environments, traditional perimeter defenses no longer suffice. Zero Trust Security minimizes breach impact by ensuring continuous verification and least-privilege access across users and systems.
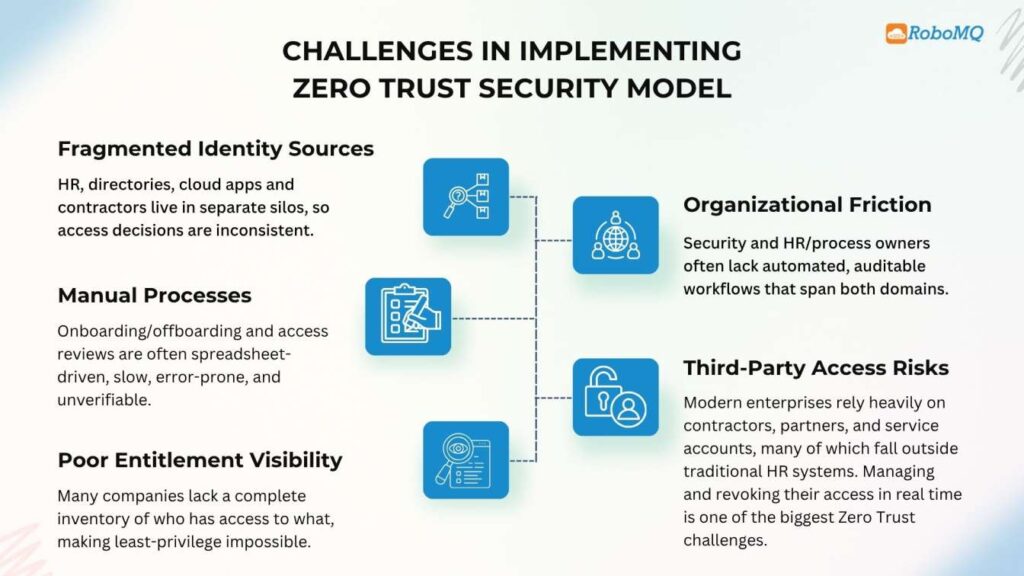
Organizations often face fragmented identity systems, manual access reviews, lack of real-time visibility, and poor integration between HR and IT systems.
IGA enforces least-privilege access, automates provisioning and deprovisioning, and ensures continuous access review. These capabilities make IGA the operational backbone of a Zero Trust Security framework.
Hire2Retire automates identity lifecycle management, ensuring every access change is triggered by authoritative HR events. This eliminates orphaned accounts and enforces least-privilege access at scale.
Enterprises implementing H2R typically see reduced provisioning time, faster offboarding, fewer audit exceptions, and stronger compliance. All of these benefits directly support and enable Zero Trust Security.