Cybercrime is no new paradigm. 52% of vulnerabilities observed by CrowdStrike in 2024 were related to initial access. Attacks are most dangerous when privileged accounts become prey to them. These accounts hold the most sensitive information and critical systems.
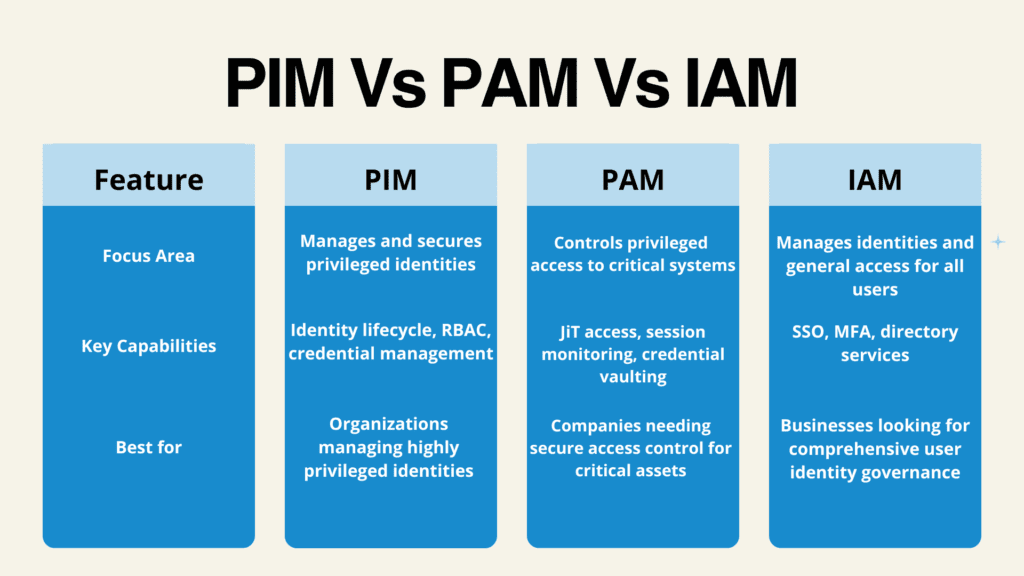
Privileged Identity Management (PIM) is a branch of Identity and Access Management (IAM) that focuses on managing user accounts that have privileged access within an organisation.
PIM does this by implementing controls for privileged identities so that privileged credentials are assigned only temporarily and when absolutely required. As soon as the task that demands privileged access is done, the access privileges are instantly removed. This least privilege principle prevents anyone from having constant access to critical systems unless required. It prevents systems and data from being accessed on “need-to-basis” and “need-to-know”.
An Identity and Access Management (IAM) system assists an organization in controlling who has access to what so that all users are correctly authenticated and only view the information or systems they should. It includes all of the users throughout the company, including employees and contractors.
All of this is within the larger IAM context, though. Privileged Identity Management (PIM) and Privileged Access Management (PAM) go a step further still. These are aimed specifically at privileged accounts those with high levels of privilege that can make life-changing modifications to applications, networks, or servers.
The main distinction is what they focus on: PIM controls and tracks the access already possessed by privileged accounts, but PAM regulates how that privilege is issued, utilized, and followed every time an individual makes a request to use sensitive systems. They work together as the foundation of a secure, properly governed IT infrastructure.
Companies making use of PIM and privilege administration can protect their worlds with a number of key features:
RBAC provides IT administrators the ability to create and manage roles that define what kind of access privileges each user has within the system. With PIM, roles are extremely flexible, so that users are only granted the privileges they require, minimizing unneeded risk.
PIM provides temporary privileged access according to pre-defined policies. This way, users don’t possess constant privileged credentials, reducing the possibility of security threats and providing just enough access, employing temporary credentials like tokens, keys and passwords.
Most PIM systems, such as those employed in privileged access management, also have an approval process before privileged access is granted. This monitoring guarantees accountability and less room for misuse, especially within organizations that have global administrators working on sensitive systems.
All operations performed under privileged accounts are being monitored and recorded, specifically with the emphasis on privileged account activity. These include extensive audit trails, session recording, and alerting, which assist in the recognition of suspicious activity when executing privileged tasks.
PIM will automatically take away the access rights once the user has finished performing a task that needs privileged access. This lessens the attack surface by preventing any user from having residual privileges they don’t need.
Though PIM and privileged access management are excellent instruments, they both pose challenges:
Implementing PIM for large enterprises having thousands of privileged accounts might be complicated. Organizations need to make sure that they have a solid strategy for role assignment, access management, and approval workflows.
Most organizations have operations in on-premises as well as cloud environments. Access privilege and privileged account management across hybrid environments is a careful planning activity.
Users used to constant privileged access might be resistant to change towards just-in-time models. It is important to educate users on the value of PIM and privileged account management for seamless adoption.
Identifying your organization’s most critical systems, applications, and data is the first step and determining who has access to them. This gives you a clear understanding of possible vulnerabilities.
Understanding this forehand helps in spotting issues like over-provisioned users or outdated permissions, so you can apply tighter PIM controls and reduce the risk of misuse or data breaches.
A lifecycle-driven access platform like Hire2Retire can make this process more seamless by automatically syncing employee role and access changes across systems, ensuring privileges remain accurate and up to date.
It defines the base for the privileged accounts for access ahead of time.
Implement role-based access control (RBAC) to provide end users with only what they require to carry out their tasks. With addition of a well-defined approval processes such as in Hire2Retire helps to keep an eye and be accountable across groups.
By allowing only the access required to finish a given task, you can implement least privilege access. Just-in-time (JIT) access, which automatically expires when no longer required, should be used in place of always-on administrative rights.
This guarantees that users have only the permissions they actually need to operate and reduces the possible harm of compromised accounts.
The automation features of Hire2Retire also aid in enforcing least-privilege access by guaranteeing that privileges are promptly modified in response to changes in roles or responsibilities.
Use multi-factor authentication (MFA) on privileged accounts to add an extra layer of security on top of passwords. With MFA, even if a hacker steals your password, they still won’t be able to get in without a second thing to prove they are you. Add this to good password habits, like making passwords long and hard to guess, changing them regularly, and not using the same ones on different sites, to create a strong way to verify people.
If you can’t see what is going on, you can’t keep it safe.
Use PIM tools to watch and keep track of privileged sessions as they happen. These records give a full picture of who did what and when, which is important for both rules and emergencies. Thorough tracking not only helps with laws like GDPR and HIPAA, but also makes us more accountable.
Even the best tools cannot beat users who do not know what they are doing. Routinely show users and admins what the rules are for access, how to make strong passwords, how to stop phishing, and how to deal with privileged passwords the right way.
When people get why we need security, they are more likely to follow them, which makes us safer from mistakes made by humans.
Hackers change things all the time, so should your security. Watch privileged activity all the time to find strange things and change your PIM rules as needed. Do periodic checks and risk assessments so that your controls stay useful, current, and fit with new rules.
Security is not just a task for IT; it is a group effort.
Urge openness, responsibility, and sharing of the work when it comes to privileged access. When each user knows how they play a part in safeguarding sensitive systems, PIM becomes more than a task it turns into what your group does. Privileged Identity Management is no longer a choice for big groups it is the base of today’s security. By using the rule of least privilege, making people use strong authentication, watching what happens all the time, and building a culture of responsibility, groups can cut down on the risks that come from privileged access. A well-run PIM system not only keeps your key systems and data safe, but also makes trust, safety with rules, and better leadership.
Privileged Identity Management is no longer optional for large organizations it’s a cornerstone of modern cybersecurity. By applying the principle of least privilege, enforcing strong authentication, continuously monitoring activity, and cultivating a culture of accountability, organizations can drastically reduce the risks associated with privileged access.
A well-implemented PIM framework not only protects critical systems and data but also builds trust, ensures regulatory compliance, and strengthens overall governance.
Ready to upgrade the Privileged Identity Management at your Organisation?
Look for solutions that offer strong access control, automation, scalability, compliance support, and easy integration with your existing systems. Evaluate based on security capabilities, user experience, and total cost of ownership.
Most modern PIM solutions provide APIs or native connectors for integration with IAM systems and directories like AD or Azure AD, enabling centralized management of privileged accounts and automated provisioning.
A robust PIM solution should include just-in-time access, session monitoring, role-based access control, approval workflows, auditing, and reporting to ensure secure and compliant privileged access.
Common challenges include complex integrations, user resistance, lack of visibility into existing privileges, and balancing security with operational efficiency during rollout.
Leading PIM platforms include Microsoft Entra PIM, Hire2Retire by RoboMQ, CyberArk, BeyondTrust, Delinea, and ManageEngine PAM360 — each offering distinct strengths in automation, scalability, and compliance.

Tanvi Mehata is a Marketing Specialist at RoboMQ with a strong technical background and extensive marketing experience, making her a perfect fit for SaaS and B2B companies. Passionate about product marketing, she crafts compelling stories that highlight business value and drive customer engagement, helping organisations connect with their audiences in meaningful ways.