Posted onNovember 11, 2025
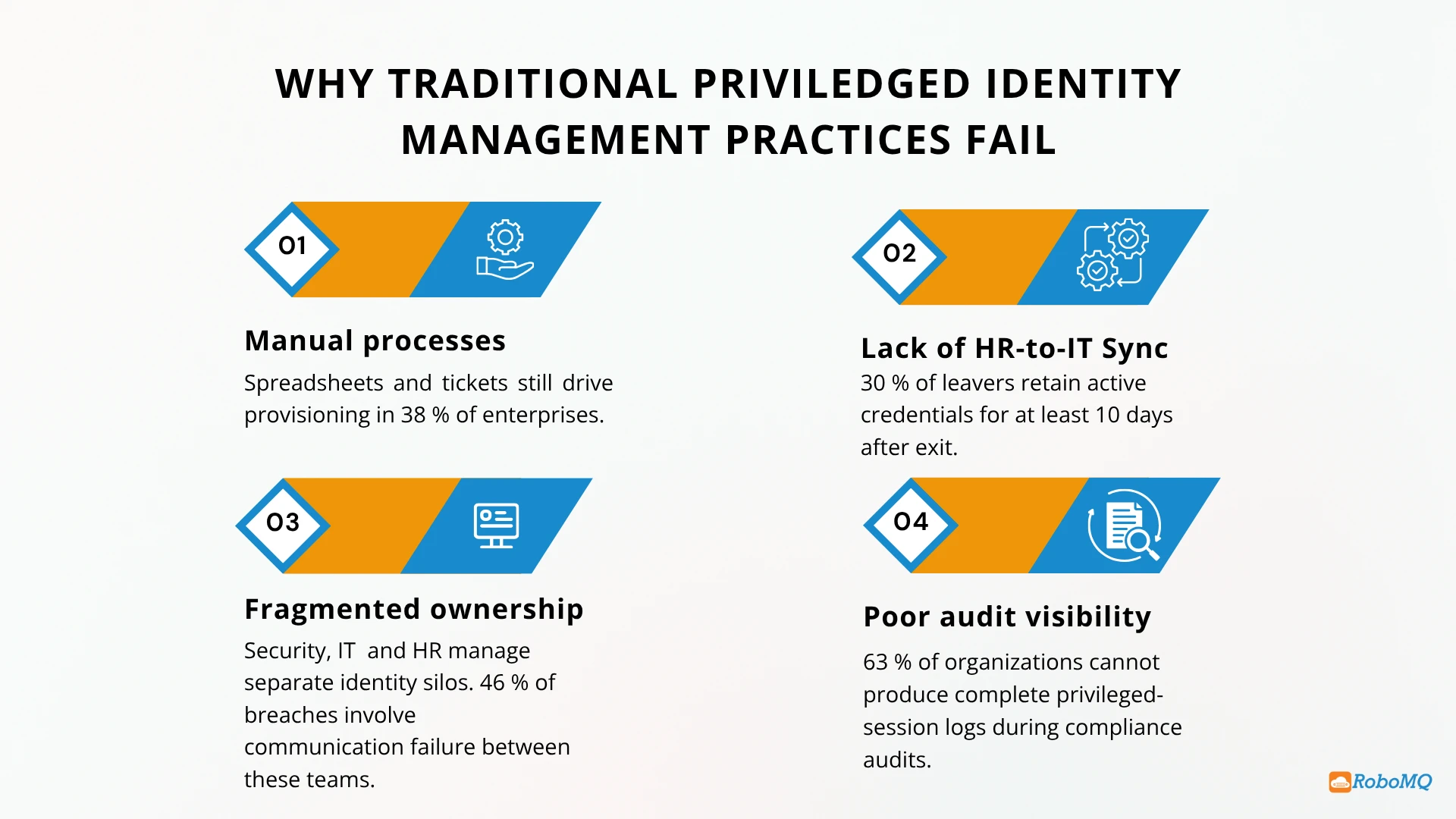
How To The Cost of Failed Privileged Identity Management Use Cases Abhishek Surtanya November 11, 2025 Privileged identity management has become the need of the hour for enterprises. One compromised privileged account can trigger a chain reaction: operational...

The Critical Role of IGA in Zero Trust Strategy
Posted onNovember 4, 2025
How To The Critical Role of IGA in Zero Trust Strategy Use Cases Abhishek Surtanya November 4, 2025 The imperative for zero trust strategy is no longer theoretical. Recent industry research shows organizations facing rapidly rising breach costs, which reached roughly...

Hire2Retire Phase 9.4: Workforce360 Reporting and RBAC, DOMO and Relias support, and More
Posted onNovember 3, 2025
New Releases Hire2Retire Phase 9.4: Workforce360 Reporting and RBAC, DOMO and Relias support, and More November 3, 2025 At RoboMQ, we’re committed to keeping Hire2Retire at the forefront of employee lifecycle automation. With the launch of Hire2Retire Phase 9.4, we’ve...

Hire2Retire Phase 9.3: SIP Addresses, Termination Lifecycle Handling in Paycor Onboarding, and More
Posted onOctober 1, 2025
New Releases Hire2Retire Phase 9.3: SIP Addresses, Termination Lifecycle Handling in Paycor Onboarding, and More October 1, 2025 At RoboMQ, we’re committed to keeping Hire2Retire at the forefront of employee lifecycle automation. With the launch of Hire2Retire Phase...

SCIM User Provisioning: The Key to Achieving Onboarding Automation
Posted onSeptember 30, 2025
How To SCIM User Provisioning: The Key to Achieving Onboarding Automation Use Cases Cameron Macaulay September 30, 2025 Manual user provisioning across a massive software stack is a constant IT problem that’s not going away. IT Leaders worldwide have a simple choice:...